There are primarily two ways that a mobile device (such as an iPhone, iPad, or Android device) can become compromised: either online – via malware, virus, or a malicious app; or by someone physically obtaining access to your device and either using it directly or copying data from it. The steps below will protect your device from the most common remote and physical threats, in order to protect your data and privacy.
Contact your college or business unit IT department for more information. Your IT staff can help you better understand how to make your device more safe and implement the below steps.
- Install OS Updates
- Keep your Apps Up to Date
- Set a Passcode and use Biometric Security
- Don’t Jailbreak or Root
- Enable Find My Device
- Backup
- Encryption
- Perform a Security Check-Up
1.Install OS Updates
Apple and Google provide frequent updates to the base operating system – Android or iOS – of your device. These updates fix bugs that can cause your device not to work right and they also fix security vulnerabilities that attackers can use to take over your device or steal your data. It is important to install these updates very soon after they are released, because attackers will often ‘reverse engineer’ the patches to discover the vulnerabilities that have been fixed, which provides a roadmap for them to attack unpatched devices.
Modern Android devices have three kinds of system updates: Android system updates, security updates, and Google Play system updates (which are separate from the Google Play Store). The latter two categories of updates should install automatically, and more information can be found at the link below.
Best practice is to enable system automatic updates, so your device will update itself automatically when patches are released:
- For iOS: Update your iPhone or iPad
- For Android: Check & update your Android version
It is crucial that your device be able to run the most recent updates to the phone’s OS. Availability of updates is dependent on the device manufacturer, and updates are usually only available for a few years after the device is released. This means phones and tablets more than a few years old probably cannot be updated, and thus cannot be secure. Once a device is no longer supported with updates, it’s time to get a new one. When purchasing a device, it is helpful to look into the manufacturer’s policy on how long they support the device with updates. Sometimes even different model lines from the same company have different support lifetimes, so it can take some digging to figure out.
- For iOS: iPhone models compatible with iOS 17
- For Android (Google Pixel only): Learn when you’ll get software updates on Google Pixel phones
2.Keep your Apps Up to Date
The apps on your device sometimes have bugs and security or privacy vulnerabilities, much like the base Android or iOS can. The developers of your apps frequently release updates to resolve these security vulnerabilities and add new functionality. Because the typical phone or tablet has so many apps installed, it is likely that some could pose a security problem at any given time. So just like with the base OS, it is important to frequently update apps as well. Fortunately, the app stores for both Android and Apple make this easy, and even offer options to automatically install updated apps when they become available. Enabling automatic updates for installed apps is recommended.
- For iOS: How to manually update apps on your Apple device
- For Android: How to update the Play Store & apps on Android
3.Set a Passcode and use Biometric Security
The first thing someone will do if they find your phone or tablet is trying to use it. They might just want to benignly make a phone call, but they could also hunt around in your messages, photos, or other data to invade your privacy. If you use a mobile payment service, they could use that to make purchases, and if you have mobile banking or finance apps, they might use them to access those accounts.
The first step to frustrate this is to set a passcode and make use of the biometric capabilities of your phone. The passcode is the real security and should be as long and complicated (random) as you can make it. Most devices also support using an alphanumeric password or passphrase, which is even stronger than just a PIN. Using an alphanumeric password is recommended, as it can frustrate attempts by malicious actors to watch as you enter your password on the small keyboard.
Since it can be tedious to constantly type a password or passphrase on a small device, many devices include a convenient biometric mechanism to unlock the phone – such as a fingerprint or face recognition. These are usually moderately secure and will require you to enter your full passcode periodically or when the device is restarted to enhance security. There is usually a setting to allow the device to automatically erase itself if the passcode is repeatedly entered incorrectly. This is to prevent someone from trying to guess your passcode to break in and is strongly recommended. Automatic screen locks also add a layer of security when you have a passcode/password enabled. You should set your phone to automatically lock after a few minutes.
- For iOS: Set a passcode on iPhone
- For iOS: Set up Face ID on iPhone
- For Android: Set screen lock on an Android device
4.Don’t Jailbreak or Root
Jail breaking or ‘rooting’ your phone means disabling the built-in security controls that would normally allow your phone to only run software downloaded from the official app store. Apple and Google provide strict security and privacy requirements for apps distributed through their app stores and have mechanisms to verify the apps that developers upload. By circumventing the official app stores to install software, you lose those protections. This means other kinds of apps can run on your phone if it’s rooted or jailbroken – viruses and other malicious software that attackers could use to steal your data or spy on you! Besides the security vulnerabilities, if done wrong, jailbreaking could damage your phone and the vendor won’t provide help because jailbreaking/rooting voids warranties.
- Learn more here: Unauthorized modification of iOS
5.Enable Find My Device
Google and Apple offer a way for users to find their lost or stolen devices. For Google, it’s Find My Device and for Apple it’s Find My. This feature can show you the exact location of your device on a map, and gives you the option to have it make a sound, display a message to help someone return it to you, or even erase your phone to completely prevent anyone from accessing your data. Depending on your device, you might also be able to enable Activation Lock, which prevents someone that steals or finds your phone from enabling their own cell service on your phone – which is an extra deterrent to phone theft.
- For iOS: Find My Support
- For Android: Be ready to find a lost Android device
6.Backup
No phone is indestructible or impossible to lose, which is why it is important to back up your device. In the event your phone is lost or stolen, you can remotely wipe that phone and retrieve your data on your new phone. Backing up your data gives you peace of mind because you know that if an accident happens, you have access to your data no matter what.
- For iOS: How to back up your iPhone, iPad, and iPod touch
- For Android: Back up or restore data on your Android device
7.Encryption
Without encryption enabled, a sophisticated attacker could access the data on your device even without the password. Fortunately, modern phones and other devices include encryption capabilities – and these have no impact on performance or usability of your device. All iPhones since iOS version 8 (released in 2014) and most current Android phones enable encryption by default. However, given the variety of Android device manufacturers and capabilities, you should check your phone to be sure.
- For iOS: Encryption and Data Protection Overview
- For Android: Android File-Based Encryption
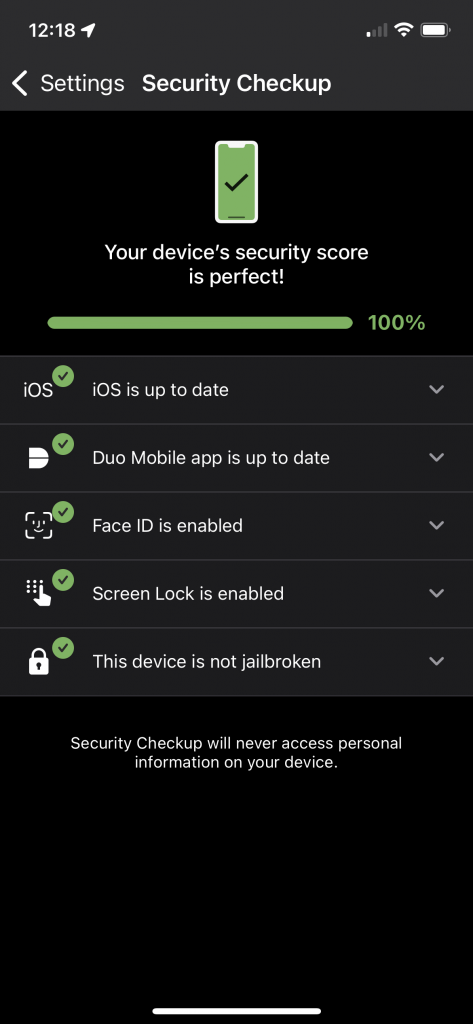
8.Perform a Security Check-Up
The DUO Mobile app used by UF to secure your Gatorlink account also has a feature that performs a quick check of many of the security settings we recommend. Access the Security Checkup from the menu of the DUO Mobile app on your device and make sure all of the items have a green checkmark. It will also provide advice on how you can fix any problems it finds.
- Instructions here: Duo Mobile security check